hankyoreh
Links to other country sites 다른 나라 사이트 링크
Snowden leaks: South Korea’s North Korea program a target of “double hacking”
The “double hacking” of a South Korean intelligence organization’s North Korea hacking program by the US National Security Agency (NSA) around 2006 is drawing renewed attention. While there had been many previous allegations of monitoring even among friendly intelligence agencies, it marked the first documented case.
One of the Snowden documents, titled “Is there ‘fifth party’ collection?,” is designed in a question-and-answer format as part of an NSA operational manual, with one employee asking questions about sigint (signals intelligence) and another answering them. Dated January 8, 2007, it was first made public in January of this year by the German weekly Der Spiegel. A portion of the document was shared in some reports at the time by the South Korean and international press, but little was known of the hacking against South Korea.
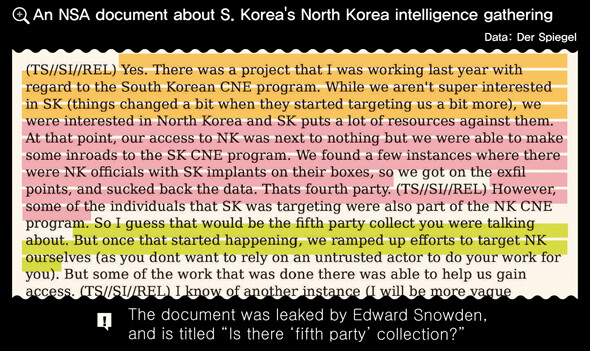
In the document, the NSA staffer answering questions states, “There was a project that I was working last year with regard to the South Korean CNE [Computer Network Exploitation] program. While we [the NSA] aren’t super interested in SK (things changed a bit since they started targeting us more), we were interested in North Korea and SK puts a lot of resources against them.”
“At that point, our access to NK was next to nothing, but we were able to make some inroads to the SK CNE program,” it continues. “We found a few instances where there were NK officials with SK implants on their boxes, so we got on the exfil points, and sucked back the data. Thats [sic] fourth party.”
Elsewhere, the documents described fourth party intelligence gathering as “passively or actively obtaining data from some other actor’s CNE activity against a target.”
The document goes on to state that the US changed its policy from hacking South Korea to hacking North Korea directly because of target trust issues.
“[S]ome of the individuals that SK was targeting were also part of the NK CNE program. So I guess that would be the fifth party collect you were talking about,” the response reads.
“But once that started happening, we ramped up efforts to target NK ourselves (as you dont [sic] want to rely on an untrusted actor to do your work for you),” it continues.
It remains unclear exactly what the meaning of fifth party intelligence collection is. From the context, it appears to suggest that North Korean intelligence hacked into computer belonging to a North Korean public official who was also being hacked by the South. No further information is given on why that person would have been a “double target” for both South and North Korean intelligence.
Meanwhile, many have called the South Korean National Intelligence Service‘s sigint “potential” surprisingly strong.
“We know that South Korea determined that the Sony hack was North Korea’s work by implanting a hacking code in North Korea,” said a university professor and security expert.
“That‘s the extent of [the NIS’s] capabilities. It’s nothing to sniff at,” the professor added.
The service is also recognized at home for its capabilities, tapping skilled civilian hackers as agents. Sigint duties are reportedly handled by the scientific intelligence bureau under the organization’s third vice director.
At the same time, the NIS does not to be channeling manpower and money into sigint according to any long-term forecast.
“Scientific intelligence isn‘t treated as well within the NIS as its importance would warrant,” said one former intelligence agent.
Another security expert with experience working with the NIS said the “individual staffers are capable, but the coordination capabilities seem lacking.”
Adding to the NIS’s poor organizational reputation is a string of high-profile operational failures. In one case during the Snowden story, it was belatedly learned that the names and positions of three agents who had been disguised as diplomats in Australia had been leaked to Australian courts and media in 2013. In 2011, an ethnically Korean employee of the Australian Department of Agriculture was caught by local intelligence contacting four NIS agents in the guise of a diplomat at the South Korean embassy in Canberra. The agent in question defied administrative measures from his organization, and the activity of South Korean NIS agents became a major issue in the trial.
A copy of the federal court ruling for the employee‘s trial was supplied to the Hankyoreh by freelance reporter Philip Dorling. In it, a bureau director with the Australian Security Intelligence Organisation (ASIO) is quoted as saying in an affidavit that South Korea had requested the ASIO “do all in its power” to prevent word of NIS activities in Australia from getting out.
In response, the court argued that revealing the names of the NIS agents would better serve Australia’s security interests, and the names of the three staffers were included in the ruling: the agents disguised as embassy employees were listed as “Mr. Hoo-Young Park,” “Mr. Bum-Yoen Lee,” and “Sa-Yong Hong,” while the other agent was listed only as “Mr. Kim.”
When asked about its handling of the case, the NIS said it “could not confirm.”
By Choi Hyun-june and Ko Na-mu, staff reporters
Please direct questions or comments to [english@hani.co.kr]

Editorial・opinion
![[Column] Park Geun-hye déjà vu in Yoon Suk-yeol [Column] Park Geun-hye déjà vu in Yoon Suk-yeol](https://flexible.img.hani.co.kr/flexible/normal/500/300/imgdb/original/2024/0424/651713945113788.jpg) [Column] Park Geun-hye déjà vu in Yoon Suk-yeol
[Column] Park Geun-hye déjà vu in Yoon Suk-yeol![[Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent [Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent](https://flexible.img.hani.co.kr/flexible/normal/500/300/imgdb/original/2024/0424/7317139454662664.jpg) [Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent
[Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent- [Guest essay] The real reason Korea’s new right wants to dub Rhee a founding father
- [Column] ‘Choson’: Is it time we start referring to N. Korea in its own terms?
- [Editorial] Japan’s rewriting of history with Korea has gone too far
- [Column] The president’s questionable capacity for dialogue
- [Column] Are chaebol firms just pizza pies for families to divvy up as they please?
- [Column] Has Korea, too, crossed the Rubicon on China?
- [Correspondent’s column] In Japan’s alliance with US, echoes of its past alliances with UK
- [Editorial] Does Yoon think the Korean public is wrong?
Most viewed articles
- 1‘We must say no’: Seoul defense chief on Korean, USFK involvement in hypothetical Taiwan crisis
- 2Will NewJeans end up collateral damage in internal feud at K-pop juggernaut Hybe?
- 3[Column] Park Geun-hye déjà vu in Yoon Suk-yeol
- 4Why Korea shouldn’t welcome Japan’s newly beefed up defense cooperation with US
- 5Thursday to mark start of resignations by senior doctors amid standoff with government
- 6N. Korean hackers breached 10 defense contractors in South for months, police say
- 7[Guest essay] The real reason Korea’s new right wants to dub Rhee a founding father
- 8[Column] ‘Choson’: Is it time we start referring to N. Korea in its own terms?
- 9Kim Jong-un expressed ‘satisfaction’ with nuclear counterstrike drill directed at South
- 10[Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent