hankyoreh
Links to other country sites 다른 나라 사이트 링크
Snowden leaks: Lack of homegrown equipment leaves S. Korea vulnerable to hacking
Many believe that the ability of the US - and other members of the “Five Eyes” - to carry out indiscriminate surveillance of internet activity around the world was made possible by the US monopoly on the technology for network communications equipment.
A significant number of the documents leaked by Edward Snowden, former contractor for the US’s National Security Agency (NSA), make it all too clear that the NSA and the UK‘s Government Communications Headquarters (GCHQ) manipulated routers to collect data.
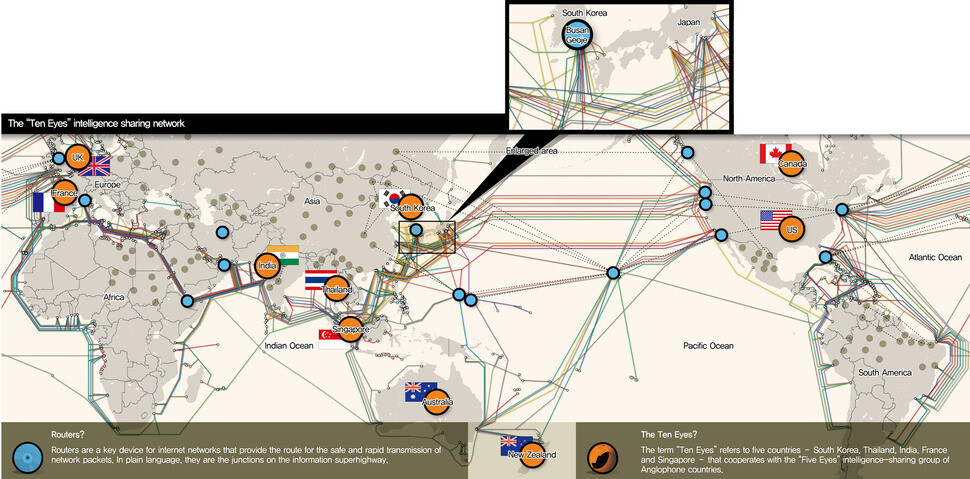
Routers are a key device for internet networks that provide the route for the safe and rapid transmission of network packets. In plain language, they are the junctions on the information superhighway.
By hacking a router, one gains control over major waypoints on the internet and can monitor the information that is passing through. This became public knowledge through the documents that Snowden leaked in 2013.
The internet began as a network linking computers in the US Pentagon. Since the US has taken the lead in internet technology and regulations, US companies have achieved dominance in the industry that produces network technology for the internet.
The sections in the Snowden documents that describe how routers are manipulated are shocking. They note how GCHQ’s attempts to hack into networks through routers have been greatly assisted by reverse engineering software. These methods enabled the intelligence agency to use Cisco routers to access “almost any user of the internet” in Pakistan, according to a highly classified memo that the GCHQ sent to the UK’s Foreign Office in July 2008.
The implication is that a British intelligence organization was able to use routers made by Cisco, an American company, to monitor internet traffic in Pakistan. This information was also made public in a BBC interview with Snowden that was broadcast on Nov. 5.
Another document in the Snowden cache says that hacking bigger routers made by Cisco, Juniper Networks, and Huawei “has been good business for us and our 5-eyes partners for some time now.”
The document goes on to list some of the things that become possible when a router is hacked. “You could add credentials, allowing yourself to log in at any time you choose. You could add/change routing rules. You could set up a packet capture capability . . . imagine running Wireshark on an ISP’s infrastructure router. . . like a local listening post for any credentials being passed over the wire(!)”
According to the book “No Place to Hide,” published in May 2014 by journalist Glenn Greenwald, the NSA intercepts Cisco packages of routers being sent overseas at American airports, installs “backdoors” that enable surveillance, and then repackages them for export.
“Such operations involving supply-chain interdiction are some of the most productive operations in TAO [Tailored Access Operations],” one of the documents says.
The evidence in the Snowden documents suggesting that routers were being hacked rocked the IT industry. The publication of documents containing allegations that the NSA had hacked Cisco routers in May 2014 got a sharp reaction from Cisco, which sent an open letter of protest to US President Barack Obama. In the first quarter of this year, Cisco had a 51% share of the global router market.
“If these allegations are true, these actions will undermine confidence in our industry,” wrote John Chambers, then CEO of Cisco, in the letter. “Cisco does not work with any government, including the United States Government, to weaken our products.”
The allegations of hacking routers also erode the moral high ground often claimed by the US.
The US government has frequently accused China of being the primary culprit in online hacking. In 2012, the US even took measures to block the import of network equipment made by Chinese companies Huawei and ZTE, citing the possibility that backdoors had been installed in them.
The documents leaked by Snowden last year reveal the US duplicity on this issue.
The problem is that the majority of routers that are being used in South Korea are manufactured in the US. A fact-finding survey of the network equipment industry conducted last year by the Korea Association of Network Industries (KANI) found that the South Korean manufacturers of routers had a 0% share in the cable network market. In other words, 100% of routers are made overseas, presumably in the US.
For high-capacity core routers in particular, the South Korean market is dominated by products by American companies Cisco and Juniper.
According to a 2012 report by the Korea Institute of Civil Engineering and Building Technology, all seven of the international routers in KT’s Hyehwa Telephone Office, located in Seoul, which handles half of international internet traffic in the country, are products of Cisco or Juniper.
The Hankyoreh asked the Ministry of Science, ICT and Future Planning and the main three telecoms to provide specifics about the routers currently in their possession, but this request was denied on the grounds of being a “business secret.”
“South Korea relies on other countries for most of its network equipment. Given the fact that there are no national borders or allies in the online information war, there’s a critical need to carry out research in the area of network security,” said Kang Seok-yeol, former director of the NSRI (National Security Research Institute).
By Choi Hyun-june, staff reporter
Please direct questions or comments to [english@hani.co.kr]

Editorial・opinion
![[Guest essay] Preventing Korean Peninsula from becoming front line of new cold war [Guest essay] Preventing Korean Peninsula from becoming front line of new cold war](https://flexible.img.hani.co.kr/flexible/normal/500/300/imgdb/original/2024/0507/7217150679227807.jpg) [Guest essay] Preventing Korean Peninsula from becoming front line of new cold war
[Guest essay] Preventing Korean Peninsula from becoming front line of new cold war![[Column] The state is back — but is it in business? [Column] The state is back — but is it in business?](https://flexible.img.hani.co.kr/flexible/normal/500/300/imgdb/original/2024/0506/8217149564092725.jpg) [Column] The state is back — but is it in business?
[Column] The state is back — but is it in business?- [Column] Life on our Trisolaris
- [Editorial] Penalties for airing allegations against Korea’s first lady endanger free press
- [Editorial] Yoon must halt procurement of SM-3 interceptor missiles
- [Guest essay] Maybe Korea’s rapid population decline is an opportunity, not a crisis
- [Column] Can Yoon steer diplomacy with Russia, China back on track?
- [Column] Season 2 of special prosecutor probe may be coming to Korea soon
- [Column] Park Geun-hye déjà vu in Yoon Suk-yeol
- [Editorial] New weight of N. Korea’s nuclear threats makes dialogue all the more urgent
Most viewed articles
- 1Behind-the-times gender change regulations leave trans Koreans in the lurch
- 2Yoon’s revival of civil affairs senior secretary criticized as shield against judicial scrutiny
- 3Unexpected rate of AI development requires timely discussion of side effects
- 4Family that exposed military cover-up of loved one’s death reflect on Marine’s death
- 5Marines who survived flood that killed colleague urge president to OK special counsel probe
- 6Japan says its directives were aimed at increasing Line’s security, not pushing Naver buyout
- 7A breath of fresh air: Innovative architecture in the time of COVID-19
- 8‘Weddingflation’ breaks the bank for Korean couples-to-be
- 9South Korean ambassador attends Putin’s inauguration as US and others boycott
- 10Mother of Sewol victim travels 3,100km in 21 days to raise awareness about investigation into ferry